Importance of Cloud Security :
Security in cloud computing is critical for any organization that wants to keep its apps and data safe from malicious attackers. Maintaining a good cloud security posture assists enterprises in reaping the advantages of cloud computing.
More and more organizations are adopting cloud based security solutions as cloud security comes with its own set of benefits like
- Lower upfront cost
- Lower operational Cost
- Lower administrative costs,
- On-demand Scalability
- Higher Stability and Availability
- Enhanced DDoS protection.
Main Categories of Cloud Security Solutions
- Cloud workload protection platform (CWPP)—a consolidated system for increasing visibility into cloud resources, especially for the purpose of securing cloud workloads. CWPP lets you perform security functions in more than one environment. Using CWPP you can protect workloads such as
- Containerized Applications
- Serverless Applications
- Applications running in Cloud Instances
- Cloud based API Endpoints
- Cloud based storage and databases
- Cloud security posture management (CSPM)—solutions keep inspecting cloud environments and warns about software configuration vulnerabilities and compliance risks. These risks can be due to human error or oversight. CSPM assists in the prevention of software configuration vulnerabilities and compliance issues performing following activities.
- Monitoring creation and modification of resources across cloud.
- Ensures consistent implementation of policies for cloud resources.
- Scan compute resources for any misconfiguration / settings that are prone for abuse.
- Risk assessment of cloud workloads using standard security frameworks.
- Cloud access security broker (CASB) – Moving to cloud increase flexibility for employees and IT Team but also introduces new challenges for keeping organization secure. This is where a CASB solution steps up and act as a gatekeeper to broker access in real time between enterprise users and cloud resources they use by enforcing enterprise security policies. CASBs address security gaps in an organization’s use of cloud services by providing granular visibility into and control over user activities and sensitive data. CASB coverage scope applies broadly across SaaS, PaaS, and IaaS. CASB Solution can help organizations protecting environment across the following pillars.
- Visibility: detect all cloud services; assign each a risk ranking; identify all users and third-party apps able to log in
- Data security: identify and control sensitive information (DLP); respond to sensitivity labels on content
- Threat protection: offer adaptive access control (AAC); provide user and entity behavior analysis (UEBA); mitigate malware
- Compliance: supply reports and dashboards to demonstrate cloud governance; assist efforts to conform to data residency and regulatory compliance requirements.
- Cloud data security refers to a set of software tools used to build storage access restrictions and policies that safeguard cloud-based data and applications. Cloud data security technologies may be used to do the following:
- Implement security rules consistently across several cloud storage platforms.
- Safeguard data that is stored in the cloud or transmitted to or from cloud services.
- Manage governance, assign rights, and keep track of who has access to critical data.
- Encrypt data while it is at rest and in transit.
- Prevent sensitive data from being deleted, updated, or moved outside the corporate boundaries by using data loss prevention.
- Cloud compliance—software examines cloud environments for breaches of compliance. The process is often automated, with notifications and the ability to create audits for each compliance standard.
Microsoft’s Defender for Cloud: A Key Component to Providing Reliable Cloud Security
Microsoft Defender for Cloud is an Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP) providing CSPM, CWPP capability for workloads running across cloud platforms.
Defender for Cloud helps you keep your resources and workloads safe in the cloud and on-premises by meeting three important needs:

- Defender for Cloud secure score continually assesses your security posture so you can track new security opportunities and precisely report on the progress of your security efforts.
- Defender for Cloud recommendations secures your workloads with step-by-step actions that protect your workloads from known security risks.
- Defender for Cloud alerts defends your workloads in real-time so you can react immediately and prevent security events from developing.
Defender for Cloud offers both basic and advanced security features that can help protect your organisation from threats and attacks.
- Basic Features – Defender for Cloud by default delivers fundamental cloud security and posture management (CSPM) capabilities such as secure score, security policy and basic recommendations, and network security assessment to assist you in protecting your Azure resources.

- Enhanced Features – Once Enabled, enhanced security features Defender for Cloud can provide unified security management and threat protection across your hybrid cloud workloads, including
- Microsoft Defender for Endpoint – a comprehensive EDR Solution.
- Vulnerability assessment for virtual machines, container registries, and SQL resources.
- Multi Cloud Security – You can protect your resources and workloads running on AWS & GCP Cloud platform.
- Hybrid Security – Unified console of security across all the on-premise and cloud workloads.
- Threat projection alerts
- Track compliance with a range of standards
- Access and application controls by blocking malware and unwanted applications
- Cloud-native threat protection for the Azure services common to all of your resources: Azure Resource Manager, Azure DNS, Azure network layer, and Azure Key Vault
- Real-time threat protection on your containerized environment.

Enable enhanced security features on a subscription
To enable enhanced security features on a subscription:
- Sign in to the Azure portal.
- Search for and select Microsoft Defender for Cloud.
- In the Defender for Cloud menu, select Environment settings.
- Select the subscription or workspace that you want to protect.
- Select Enable all to enable all of the plans for Defender for Cloud.
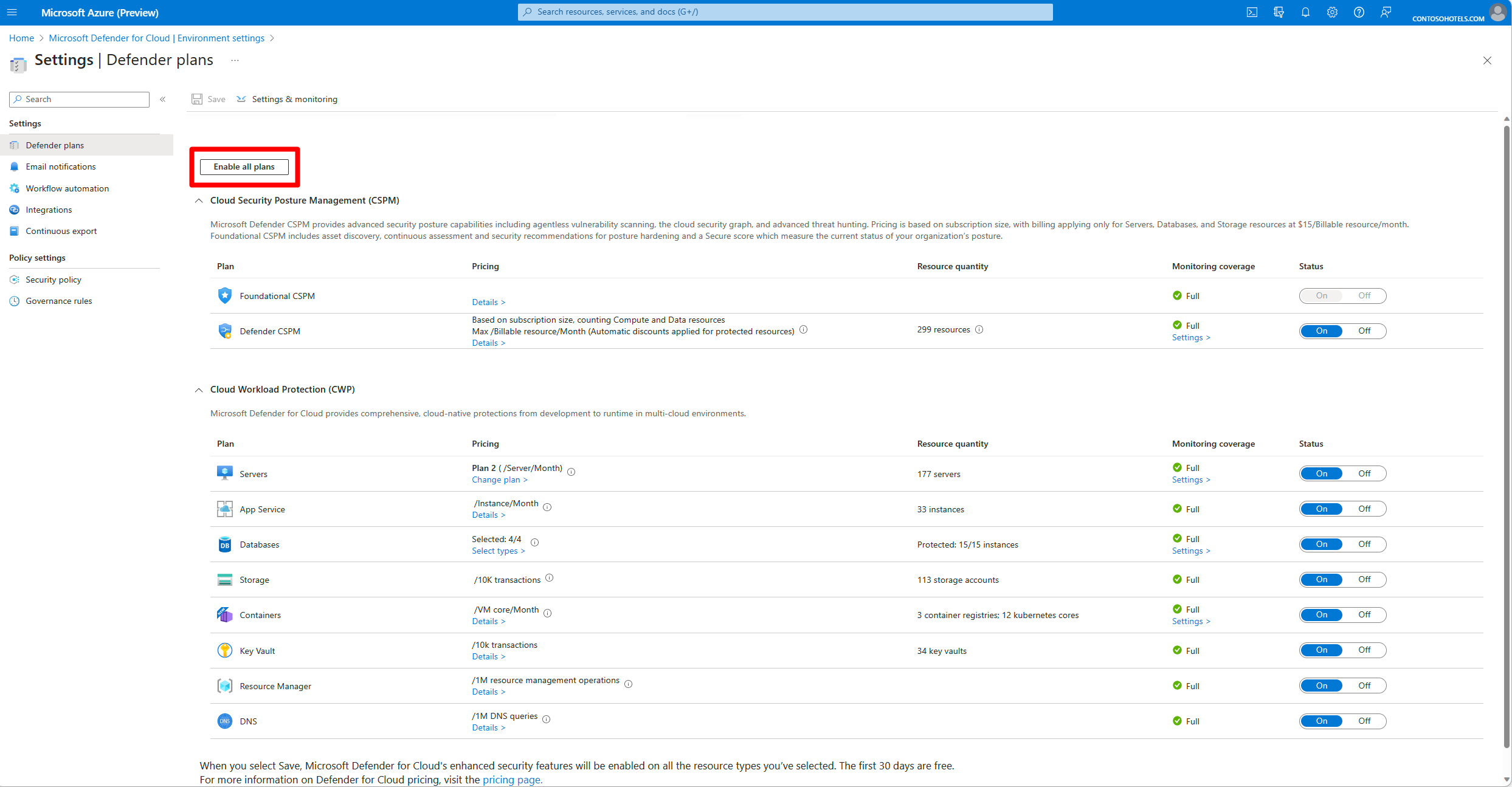
- Select Save.
I hope this will be informative for you. Please do share if you find worth sharing this.
